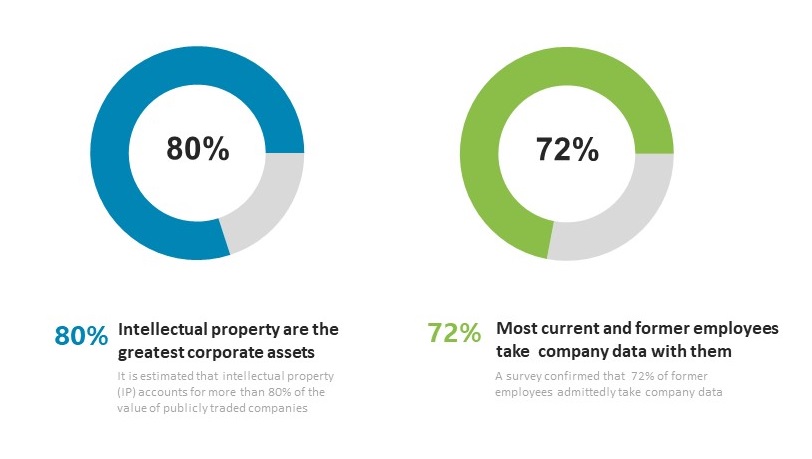
It’s estimated that intellectual property (IP) accounts for more than 80% of the value of publicly traded companies. From trade secrets and confidential corporate strategies to sensitive technology diagrams and customer databases, this information is what keeps the business alive. Consequently, the loss or unauthorized disclosure of intellectual property can have a significant negative impact on organizations. This risk has led to growing concerns around the trusted employees who have access to this data and the potential for insider threats to cause harm.
72% of former employees admittedly take company data, leaving many organizations exposed to the dangers associated with insider threats. In addition, over two-thirds of employee IP theft occurs within 90 days of an employee’s resignation announcement. Employees can then take the information to their new place of work, leverage it to start their own companies, sell it to competitors, and more. Enterprises are facing the harsh reality of failed traditional data loss prevention tactics and realizing that if and when employee data theft happens, they must be able to investigate and respond accordingly.
“72% of former employees admittedly take company data” – Info Security Magazine
Impact of intellectual property theft on businesses
The importance of intellectual property to any organization cannot be overstated. Malicious attackers, which can include internal employees, understand the value of this data. This makes it an attractive target with roughly $500 billion out of the $1.5 trillion cybercrime ring attributed to IP theft. The most common damaging effects of IP theft on businesses include reputational damage, legal ramifications, and financial losses.
When IP leaves a company, control over who has access to the data is lost. This means the data could end up in the hands of a competitor or someone seeking to sabotage your business. This can spiral into a host of consequences. For example, stolen IP can lead to counterfeiting of products, duplication of services, and more. This might lead to a decrease in sales and less income available to continue operating or growing your business. At one point, around 750,000 jobs were lost across the US as a result of IP theft, highlighting the significant downstream impacts to businesses.
Lawsuits and legal implications pose another challenge. Battling employee IP theft in court takes time and requires advanced expertise to ensure digital evidence is gathered, preserved, and presented effectively. This can get expensive for ill-prepared companies who haven’t planned ahead.
Common types of intellectual property employees take
Employees have varying motivations when it comes to intellectual property theft that can influence what they go after. A few common examples include theft of:
- Employee or customer databases that can be used to poach people in the future
- Email communications
- Financial projections and records
- Marketing and sales information
- Technology details, diagrams, and engineering schemas
- Pricing model data
- Contracts and legal documents
- And more!
How employees steal intellectual property
As the digital landscape continues to evolve, it may become necessary that you grant employees access to sensitive parts of your corporate network or databases. While this is aimed at ensuring they have all the data required to function effectively in their role, this access can also be abused by malicious insider threats. A few ways IP theft or leakage occur include employees:
- Using personal smartphones and computers to manage data through bring your own device (BYOD) programs
- Sending business emails to personal accounts
- Exporting data to USB flash drives and other portable storage devices
- Taking screenshots of sensitive data employees may not have access to export
- Sharing data on cloud storage platforms like Dropbox, Google Drive, Github, and more
- Using personal email accounts to sign up for unsanctioned third-party SaaS tools used to complete work-related tasks
Using digital forensics to uncover employee data theft
Investigating insider threats and employee data theft can be a very delicate process. Companies need to ensure none of the parties involved take any actions that limit how much evidence can be uncovered or the usability of the evidence. When planning to take legal action and avoid lawsuits from employees in the process, your ability to handle digital evidence can play a critical role in your ultimate success or failure.
What is digital forensics?
Digital forensics is the process of using technology and computer science to organize and execute investigations involving digital assets. Digital forensics is, in essence, an umbrella term that evolved from the term computer forensics and can typically include computer forensics services, mobile forensics, video and or digital picture analysis, and other mediums that store digital media. The process is comprised of four phases, including identifying sources or assets that may contain evidence, preserving the evidence throughout the entire process, analyzing the collected evidence for insights and conclusions, and finally reporting findings.
Having a qualified expert to support this effort is essential. A digital forensics investigator should be able to help you uncover what systems and data were accessed and utilized by the employee. Additionally, insider threats are known for attempting to cover their tracks, and a good investigator knows how to find evidence that may have been deleted or covered up by the employee. A typical digital forensics investigation might include activities like forensic imaging of your devices and servers, isolating emails sent to private addresses like Gmail, and locating files that may have been recently accessed, manipulated, or exported. Additional tasks might include identifying if there have been any recently attached storage devices, ascertaining whether data was copied from cloud storage platforms, determining when remote connections were established, and reviewing relevant data points. Final tasks might include reporting detailed information and conclusions, including workflows that may be relied upon in court.
Important considerations when conducting digital forensics investigations
Whether it’s a current or former associate, investigating these threats can get complicated. From considering privacy laws to ensuring that the evidence can be relied upon if the employee IP theft case goes to court, businesses should take precautions when carrying out investigations. Good starting points to consider include:
Formal permission
The company and any digital forensics investigators engaged should ensure that there is written permission to conduct the investigation and that scope has been defined. Ensure HR and legal teams are involved in the proceedings.
Internal policies
Businesses should have clear company policies that enable the digital forensics investigator to ascertain what the employee is allowed to do or not do and whether any relevant clauses support the investigation.
Compliance
Businesses should remain informed about all of the employer regulations and compliance rules the company must follow to identify limitations and special requirements associated with the investigation. This ensures that the organization’s compliance status is not at risk as a result of the investigation.
Privacy
Before investigating any insider threat or employee fraud, entities should consider all relevant local, national, and international privacy laws. For instance, some data protection acts have strict guidelines on what can be done with an employee’s data or the systems they worked with. This is especially applicable in companies with bring your own device programs looking to examine employee personal assets.
Resources
Digital forensics is a very delicate process. One wrong move can permanently erase evidence or render it inadmissible in court. Rely on experts who are experienced and highly qualified to conduct investigations. Also, plan ahead on the types of technology you need to support employee investigation such as logging and monitoring, insider threat detection software, and more.
Closing thoughts
Insider threat is a common cause of IP theft. Whether it’s a disgruntled employee who feels they deserve to own the data they created at work or the opportunistic departing employee looking to take your IP to their next job, enterprises will need to do more to mitigate this risk. Digital forensics can help uncover and understand potential theft to help your company respond quickly and efficiently.




