Knowing your environment is critical, and it is crucial to fully understand what processes are running and what they are used for. In this example, we are going to be focusing on the mictray64.exe process that comes installed in most windows updates for certain types of computers. As an end-user, you may not even know that this process is running. We are going to dig and determine if this is something that we need running in our corporate networks for the function that is provided.
*This file doesn’t try to hide or live anywhere suspicious on your machine. *
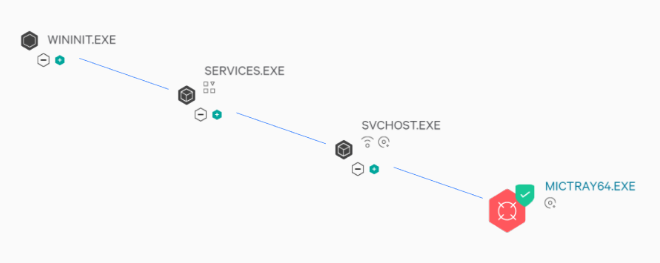
Before digging into this specific situation, I want to preface this with the reason the mictray64 is so dangerous is because of two things: first is because of how it can capture keystrokes and second is because it is a standard file that is apart of a basic Windows install on specific computers. Having the ability to monitoring your systems and network is key to detection. Being able to tell the difference between what is regular activity and malicious activity is a huge benefit in preventing these scenarios from happening in the first place. Now, let’s review what exactly the Mictray64.exe is used for.
*This should be the only process running on a normal mictray64.exe file*
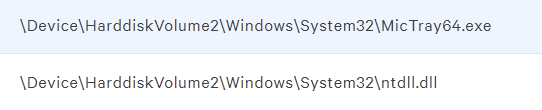
The sole purpose of the Mictray64.exe is that it is a Windows process that allows the Windows driver to respond when the users prompt for the special keys action. The problem with this process is that it sends all keystrokes to the debugging interface or to a designated log file where it stored in plain text.
Some indicators of compromise for a malicious copy of the Mictray64.exe are as follows:
- Log files being written to public user shares (by default, a legit mictray64.exe won’t do that)
- Any inbound/outbound network activity associated with the file
- The file is stored or run anywhere but the system32 location
- The only other processes observed being run in response to the mictray64.exe is the ntdll.dll file, anything else should raise a concern.
The most considerable concern is that this is a legitimate file that is signed and globally recognized. Still, due to the nature of its operation, it should be deemed malicious and removed or at least closely monitored. Let us take a deep dive look into how this file can be exploited in your environment in two different scenarios.
Scenario 1: A maliciously scripted Mictray64.exe file is used
In this first scenario, an attacker has altered the mictray64.exe file to perform additional steps outside of its intended function. The file is them blasted out to a massive email list that is specially crafted for your organization or industry. All the attacker needs are for just one of your employees to open the email and click on the malicious update button that the attacker embedded with the file. The email sent is well written and looks like a legitimate support email from Microsoft.
Let’s assume one of your employees clicks on the embedded file that is disguised as a button in the email. The file is instantly downloaded and starts to execute without the user’s constant or awareness. The mictray64.exe starts capturing all keystrokes performed by the user and then sends them to a local log file. In the meantime, the attacker has scripted the malicious mictray64.exe file to create an RDP session for him to get instant access to the user’s machine to retrieve the log file containing all the user’s keystrokes.
At this point, the attacker has a way in, plus a large file of all the user’s keystrokes. The attacker will now spend some time reviewing the log file to try and determine if there are any credentials that the user entered that might give the attacker additional access to ether other systems or sensitive data.
Scenario 2: A legit copy of mictray64.exe is installed and active. The attacker uses its output to gain access to additional resources.
In this second scenario, the mictray64.exe file is legitimate and was installed with the installation of Windows, which hasn’t been deactivated.
The attacker has gained access to your network or system utilizing a phishing email. The attacker checks the running processes on your system and notices that the mictray64.exe is running. The attacker is familiar with these processes and proceeds to exploit it y checking the default location in which the debug logs are sent. Since the file has always been active, instant access is provided to all of your previous keystrokes.
The attacker reviews the file for a while to gather what looks like credentials to your company’s AWS enterprise account. After trying the credentials, the attacker realizes that the AWS account doesn’t have MFA enabled and is granted access to that particular user’s account. From here, the attacker can continue to gather an active user list (as well as their permissions) from the AWS console to locate users with higher privileges and access to more valuable data.
Conclusion: At the end of the day, it is highly recommended to uninstall the mictray64.exe from your environment. It is essential to be mindful of any windows patching that is done after that point of deactivation, will inadvertently reinstall the mictray64.exe back onto your systems. Having an automated process in place to both detect and remove this is critical to the security of your infrastructure. If you are struggling with the means of accomplishing this task or anything incident response-related in general, take a look at what [insert name and link here] have to offer. When it pertains to the security of your organization, you should never assume, always have a way to know for sure that a threat has been neutralized to lower the overall risk in your organization.
[/vc_column_text][/vc_column][/vc_row][vc_row type=”in_container” full_screen_row_position=”middle” column_margin=”default” column_direction=”default” column_direction_tablet=”default” column_direction_phone=”default” scene_position=”center” text_color=”dark” text_align=”left” row_border_radius=”none” row_border_radius_applies=”bg” overflow=”visible” overlay_strength=”0.3″ gradient_direction=”left_to_right” shape_divider_position=”bottom” bg_image_animation=”none”][vc_column column_padding=”no-extra-padding” column_padding_tablet=”inherit” column_padding_phone=”inherit” column_padding_position=”all” column_element_direction_desktop=”default” column_element_spacing=”default” desktop_text_alignment=”default” tablet_text_alignment=”default” phone_text_alignment=”default” background_color_opacity=”1″ background_hover_color_opacity=”1″ column_backdrop_filter=”none” column_shadow=”none” column_border_radius=”none” column_link_target=”_self” column_position=”default” gradient_direction=”left_to_right” overlay_strength=”0.3″ width=”1/1″ tablet_width_inherit=”default” animation_type=”default” bg_image_animation=”none” border_type=”simple” column_border_width=”none” column_border_style=”solid”][vc_column_text][/vc_column_text][/vc_column][/vc_row]

