Threat actors are now deliberately targeting Veeam backup infrastructure to exfiltrate sensitive data before executing broader attacks.
For years, Veeam Backup & Replication has quietly supported business continuity across enterprises of all sizes. It is one of the most widely deployed data protection platforms in the world. But in 2025, Cyber Centaurs’ incident response investigations began uncovering a troubling and consistent pattern: attackers are not merely disabling backups anymore — they are actively seeking out and interacting with Veeam environments, early and deliberately.
Across healthcare, manufacturing, and technology supply chain environments, threat actors have escalated their tactics. Instead of simply encrypting production environments and removing backups to increase ransom leverage, attackers are now accessing and exfiltrating backup data itself. Veeam has become more than a backup system, it is a one-stop repository for sensitive enterprise information, and adversaries know it.
A Threat Years in the Making
The exploitation of Veeam systems is not a new phenomenon. Since at least 2020, security researchers and incident responders have noted ransomware groups and state-aligned actors probing and attacking Veeam installations.
Over the years, various critical vulnerabilities have been disclosed and patched:
- CVE-2022-26500 / CVE-2022-26501: Remote code execution vulnerabilities in Veeam Backup & Replication components.
- CVE-2023-27532: A vulnerability allowing threat actors to extract encrypted credentials stored in the Veeam configuration database. Widely exploited by ransomware groups in 2023 and early 2024.
- CVE-2024-29849 / CVE-2024-29850 / CVE-2024-29851 / CVE-2024-29852: A suite of issues enabling privilege escalation, arbitrary code execution, and backup compromise.
- CVE-2024-40711: A deserialization flaw discovered in mid-2024 and exploited in the wild by new ransomware strains by Q3 2024. This vulnerability in the Veeam RESTful API allowed unauthenticated remote code execution on servers exposed to the internet.
Each time these vulnerabilities surfaced, threat actors adapted quickly, often weaponizing proof-of-concept code within days. But 2025 brought a change in purpose: attackers weren’t just seeking disruption; they were actively harvesting what Veeam protects.
From Backups to Leverage: Why Attackers Steal Veeam Data
Backup environments are a goldmine for modern threat actors. Veeam, in particular, offers attackers a comprehensive, time-ordered, and often unencrypted mirror of an organization’s file shares, email, database snapshots, and critical servers. Instead of exfiltrating data piecemeal across dozens of compromised systems, threat actors increasingly target Veeam directly, because everything they want is already there. Several of our 2025 incident investigations revealed attackers using Veeam CLI tools to list backup contents, verify data availability, and export specific archives, all before launching encryption payloads. In some cases, exfiltrated backup data included sensitive legal documents, patient records, proprietary source code, and even emails presumed long-deleted from production systems. For adversaries operating on double-extortion or data resale models, this is a tactical advantage. The threat actor gains not only leverage but an organized index of the victim’s digital assets.
A Recognizable Pattern Across Sectors
The industries most impacted this year reflect the attacker’s preference for environments where backups are rich in data, poorly segmented, and essential for operations. In healthcare, backups often include electronic medical records (EMRs), medical imaging archives, and regulatory documentation. In manufacturing, they may include SCADA configurations, CAD files, or ERP system states. And in the technology supply chain, particularly among MSPs and infrastructure providers, backup environments are multi-tenant, making them high-value breach points.
In all three cases, we observed a consistent pattern: attackers identify Veeam servers within the first 48 hours of lateral movement, extract credentials where possible, and begin backup reconnaissance before any payloads are delivered.
The Anatomy of an Obsession
This is what distinguishes 2025 from prior years. In previous incidents, the compromise of backup infrastructure was often an afterthought, a final blow to ensure victims couldn’t recover. Today, backup systems, and Veeam in particular, are often one of the first targets, not the last. Adversaries are actively scanning for open Veeam management interfaces via Shodan, using internal enumeration tools to locate backup services on known ports (e.g., 9392), and scripting access via CLI to silently observe backup retention policies and available restore points.
Cyber Centaurs has responded to incidents where Veeam was not only accessed but used as a staging environment, where data was extracted from the backup system instead of production.
Notable References and Sector Alerts
Several high-profile advisories in the past year reinforce this growing threat:
- The Hacker News – Reported new ransomware campaigns leveraging Veeam exploits in July 2024.
- HHS HC3 Sector Alert – Urged healthcare providers to patch Veeam vulnerabilities and monitor for indicators of compromise.
- AHA Cyber Alert – Notified hospitals of exploitable flaws and exploitation in the wild.
- BankInfoSecurity – Provided analysis of patch releases and attacker TTPs related to CVE-2024-40711.
These publications, combined with direct case evidence, point to a clear conclusion: the exploitation of Veeam is accelerating — not declining.
Timeline of Veeam Exploits and Attacker Adoption
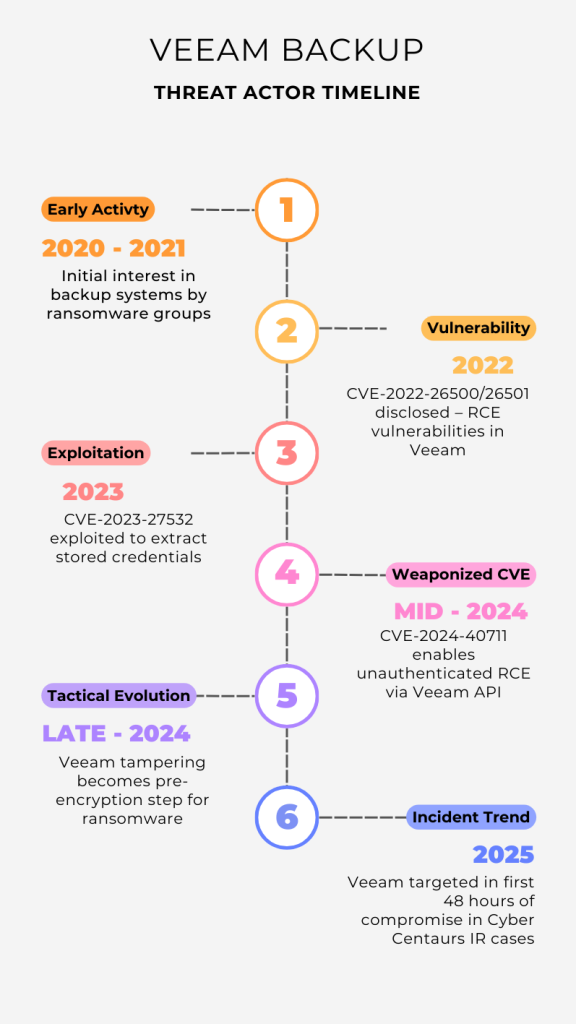
2020–2021: Initial interest in backup systems, experimentation by ransomware groups.
2022: First critical RCEs disclosed (CVE-2022-26500, etc.).
2023: CVE-2023-27532 is weaponized, used by LockBit and others.
Mid–2024: CVE-2024-40711 deserialization flaw enables RCE from internet.
Late–2024: Multiple ransomware families prioritize Veeam tampering before encryption.
2025 Q1–Q3: Cyber Centaurs sees surge in cases where Veeam is targeted within first 48 hours of intrusion.
The timeline should also show patch release dates, advisories, and real-world incidents, which future articles in this series can explore in detail.
What Comes Next
The growing fixation on Veeam is not an isolated phenomenon; it is an industry-wide risk pattern that is intensifying. Backup infrastructure, long considered a fallback or recovery measure, has now become an operational phase of modern attacks. And in 2025, that shift is both measurable and actionable.
This article is the first in a multi-part series by Cyber Centaurs examining the evolving threat landscape around Veeam and similar backup platforms. In the next article, Inside the Kill Chain – How and Why Threat Actors Target Veeam, we will walk through the technical steps attackers use to identify, enumerate, and interact with Veeam environments in real-world breaches.
Later, we’ll follow up with Exposed and Exploitable – How Misconfigured Veeam Enables Ransomware, where we explore common configuration issues that give threat actors the access they need to turn backups into vulnerabilities.
Organizations relying on Veeam must now ask a new set of questions — not just “Are we backing up properly?” but “Who can see those backups? Who can extract them? Who’s watching for abuse?”
Because if threat actors are obsessed with your backups, you need to be too.


